If you are satisfied with Cloudflare for your DNS over HTTPS goodness, great! However, Cloudflare is not the only DoH provider you see, and if you prefer something else, you can replace cloudflared with DNSCrypt. I’ve been using DNSCrypt to cover my home network subversive browsing activities (not really), and I think it’s time to upgrade.
DNSCrypt support DoH starting version 2, and it is the version that comes with Ubuntu 20.04 LTS, so we’ll use that. Just like the previous article, you can use an old CPU with X86-64 or Raspberry Pi 3 or 4 to host out DNSCrypt server. Make sure to assign a static IP address to the box.
To install DNSCrypt, do:
surfer@M5-1910:~$ sudo apt install dnscrypt-proxy
After the installation process completed, DNSCrypt should be automatically stared. Do:
surfer@M5-1910:~$ sudo systemctl status dnscrypt-proxy
● dnscrypt-proxy.service - DNSCrypt client proxy
Loaded: loaded (/lib/systemd/system/dnscrypt-proxy.service; enabled; vendor preset: enabled)
Active: active (running) since Sat 2021-01-02 02:46:18 WIB; 6min ago
TriggeredBy: ● dnscrypt-proxy.socket
Docs: https://github.com/DNSCrypt/dnscrypt-proxy/wiki
Main PID: 76173 (dnscrypt-proxy)
Tasks: 14 (limit: 19088)
Memory: 9.3M
CGroup: /system.slice/dnscrypt-proxy.service
└─76173 /usr/sbin/dnscrypt-proxy -config /etc/dnscrypt-proxy/dnscrypt-proxy.toml
Jan 02 02:46:18 M5-1910 dnscrypt-proxy[76173]: [2021-01-02 02:46:18] [NOTICE] dnscrypt-proxy 2.0.31
Jan 02 02:46:18 M5-1910 dnscrypt-proxy[76173]: [2021-01-02 02:46:18] [NOTICE] Network connectivity detected
Jan 02 02:46:22 M5-1910 dnscrypt-proxy[76173]: [2021-01-02 02:46:22] [NOTICE] Source [/var/cache/dnscrypt-proxy/public-resolvers.md] loaded
Jan 02 02:46:22 M5-1910 dnscrypt-proxy[76173]: [2021-01-02 02:46:22] [NOTICE] Firefox workaround initialized
Jan 02 02:46:22 M5-1910 dnscrypt-proxy[76173]: [2021-01-02 02:46:22] [WARNING] Systemd sockets are untested and unsupported - use at your ow>
Jan 02 02:46:22 M5-1910 dnscrypt-proxy[76173]: [2021-01-02 02:46:22] [NOTICE] Wiring systemd TCP socket #0, dnscrypt-proxy.socket, 127.0.2.1>
Jan 02 02:46:22 M5-1910 dnscrypt-proxy[76173]: [2021-01-02 02:46:22] [NOTICE] Wiring systemd UDP socket #1, dnscrypt-proxy.socket, 127.0.2.1>
Jan 02 02:46:22 M5-1910 dnscrypt-proxy[76173]: [2021-01-02 02:46:22] [NOTICE] [cloudflare] OK (DoH) - rtt: 66ms
Jan 02 02:46:22 M5-1910 dnscrypt-proxy[76173]: [2021-01-02 02:46:22] [NOTICE] Server with the lowest initial latency: cloudflare (rtt: 66ms)
Jan 02 02:46:22 M5-1910 dnscrypt-proxy[76173]: [2021-01-02 02:46:22] [NOTICE] dnscrypt-proxy is ready - live servers: 1
As you can see, a fresh installation of DNSCrypt on Ubuntu uses Cloudflare. Now, at this point, we have a couple of options. First, stick with Cloudflare, and we’ll leave DNSCrypt as is. Or second, pick different one from this list:
surfer@ruby:~$ sudo nano /etc/dnscrypt-proxy/dnscrypt-proxy.toml
Replace
server_names = ['cloudflare']
with, for example
server_names = ['iij']
and then restart the service
surfer@ruby:~$ sudo systemctl restart dnscrypt-proxy
And check the status:
surfer@ruby:~$ sudo systemctl status dnscrypt-proxy
● dnscrypt-proxy.service - DNSCrypt client proxy
Loaded: loaded (/lib/systemd/system/dnscrypt-proxy.service; enabled; vendor preset: enabled)
Active: active (running) since Sat 2021-01-02 06:41:06 WIB; 2min 57s ago
TriggeredBy: ● dnscrypt-proxy.socket
Docs: https://github.com/DNSCrypt/dnscrypt-proxy/wiki
Main PID: 147839 (dnscrypt-proxy)
Tasks: 11 (limit: 4442)
Memory: 6.7M
CGroup: /system.slice/dnscrypt-proxy.service
└─147839 /usr/sbin/dnscrypt-proxy -config /etc/dnscrypt-proxy/dnscrypt-proxy.toml
Jan 02 06:41:06 ruby dnscrypt-proxy[147839]: [2021-01-02 06:41:06] [WARNING] Multiple stamps for server [quickline]
Jan 02 06:41:06 ruby dnscrypt-proxy[147839]: [2021-01-02 06:41:06] [WARNING] Multiple stamps for server [safesurfer]
Jan 02 06:41:06 ruby dnscrypt-proxy[147839]: [2021-01-02 06:41:06] [NOTICE] Firefox workaround initialized
Jan 02 06:41:06 ruby dnscrypt-proxy[147839]: [2021-01-02 06:41:06] [WARNING] Systemd sockets are untested and unsupported - use at your own >
Jan 02 06:41:06 ruby dnscrypt-proxy[147839]: [2021-01-02 06:41:06] [NOTICE] Wiring systemd TCP socket #0, dnscrypt-proxy.socket, 127.0.2.1:53
Jan 02 06:41:06 ruby dnscrypt-proxy[147839]: [2021-01-02 06:41:06] [NOTICE] Wiring systemd UDP socket #1, dnscrypt-proxy.socket, 127.0.2.1:53
Jan 02 06:41:06 ruby dnscrypt-proxy[147839]: [2021-01-02 06:41:06] [NOTICE] [iij] OK (DoH) - rtt: 101ms
Jan 02 06:41:06 ruby dnscrypt-proxy[147839]: [2021-01-02 06:41:06] [NOTICE] Server with the lowest initial latency: iij (rtt: 101ms)
Jan 02 06:41:06 ruby dnscrypt-proxy[147839]: [2021-01-02 06:41:06] [NOTICE] dnscrypt-proxy is ready - live servers: 1
You can do multiple servers:
server_names = ['cloudflare','iij','meganerd-doh-ipv4']
..like this:
Jan 02 06:49:00 ruby dnscrypt-proxy[147888]: [2021-01-02 06:49:00] [NOTICE] Wiring systemd UDP socket #1, dnscrypt-proxy.socket, 127.0.2.1:53 Jan 02 06:49:01 ruby dnscrypt-proxy[147888]: [2021-01-02 06:49:01] [NOTICE] [cloudflare] OK (DoH) - rtt: 29ms Jan 02 06:49:01 ruby dnscrypt-proxy[147888]: [2021-01-02 06:49:01] [NOTICE] [iij] OK (DoH) - rtt: 97ms Jan 02 06:49:02 ruby dnscrypt-proxy[147888]: [2021-01-02 06:49:02] [NOTICE] [meganerd-doh-ipv4] OK (DoH) - rtt: 211ms Jan 02 06:49:02 ruby dnscrypt-proxy[147888]: [2021-01-02 06:49:02] [NOTICE] Sorted latencies: Jan 02 06:49:02 ruby dnscrypt-proxy[147888]: [2021-01-02 06:49:02] [NOTICE] - 29ms cloudflare Jan 02 06:49:02 ruby dnscrypt-proxy[147888]: [2021-01-02 06:49:02] [NOTICE] - 97ms iij Jan 02 06:49:02 ruby dnscrypt-proxy[147888]: [2021-01-02 06:49:02] [NOTICE] - 211ms meganerd-doh-ipv4 Jan 02 06:49:02 ruby dnscrypt-proxy[147888]: [2021-01-02 06:49:02] [NOTICE] Server with the lowest initial latency: cloudflare (rtt: 29ms) Jan 02 06:49:02 ruby dnscrypt-proxy[147888]: [2021-01-02 06:49:02] [NOTICE] dnscrypt-proxy is ready - live servers: 3
Or you can ask DNSCrypt to pick some for you. Here’s how my dnscrypt-proxy.toml is configured to do so:
# Empty listen_addresses to use systemd socket activation listen_addresses = [] #server_names = ['cloudflare','iij','meganerd-doh-ipv4'] #server_names = ['meganerd-doh-ipv4'] doh_servers = true require_nolog = true require_nofilter = true require_dnssec = true [query_log] file = '/var/log/dnscrypt-proxy/query.log' [nx_log] file = '/var/log/dnscrypt-proxy/nx.log' [sources] [sources.'public-resolvers'] url = 'https://download.dnscrypt.info/resolvers-list/v3/public-resolvers.md' cache_file = '/var/cache/dnscrypt-proxy/public-resolvers.md' minisign_key = 'RWQf6LRCGA9i53mlYecO4IzT51TGPpvWucNSCh1CBM0QTaLn73Y7GFO3' refresh_delay = 72 prefix = ''
As you can see, I’m asking DNSCrypt to find me a bunch of DNS servers that support DoH, does not log your activity, does not filter your queries, and has support for DNSSEC
Jan 02 07:18:13 ruby dnscrypt-proxy[148331]: [2021-01-02 07:18:13] [WARNING] [adguard-dns-unfiltered] uses a non-standard provider name ('2.>
Jan 02 07:18:13 ruby dnscrypt-proxy[148331]: [2021-01-02 07:18:13] [NOTICE] [adguard-dns-unfiltered] OK (DNSCrypt) - rtt: 250ms
Jan 02 07:18:14 ruby dnscrypt-proxy[148331]: [2021-01-02 07:18:14] [NOTICE] [faelix-ch-ipv4] OK (DNSCrypt) - rtt: 270ms
Jan 02 07:18:14 ruby dnscrypt-proxy[148331]: [2021-01-02 07:18:14] [NOTICE] [cloudflare] OK (DoH) - rtt: 32ms
Jan 02 07:18:14 ruby dnscrypt-proxy[148331]: [2021-01-02 07:18:14] [NOTICE] [scaleway-fr] OK (DNSCrypt) - rtt: 537ms
Jan 02 07:18:17 ruby dnscrypt-proxy[148331]: [2021-01-02 07:18:17] [NOTICE] [sth-doh-se] OK (DoH) - rtt: 273ms
Jan 02 07:18:17 ruby dnscrypt-proxy[148331]: [2021-01-02 07:18:17] [NOTICE] [deffer-dns.au] OK (DNSCrypt) - rtt: 125ms
Jan 02 07:18:17 ruby dnscrypt-proxy[148331]: [2021-01-02 07:18:17] [NOTICE] [jp.tiar.app] OK (DNSCrypt) - rtt: 115ms
Jan 02 07:18:18 ruby dnscrypt-proxy[148331]: [2021-01-02 07:18:18] [NOTICE] [doh-fi-snopyta] OK (DoH) - rtt: 222ms
Jan 02 07:18:18 ruby dnscrypt-proxy[148331]: [2021-01-02 07:18:18] [NOTICE] [dnslify-doh] OK (DoH) - rtt: 35ms
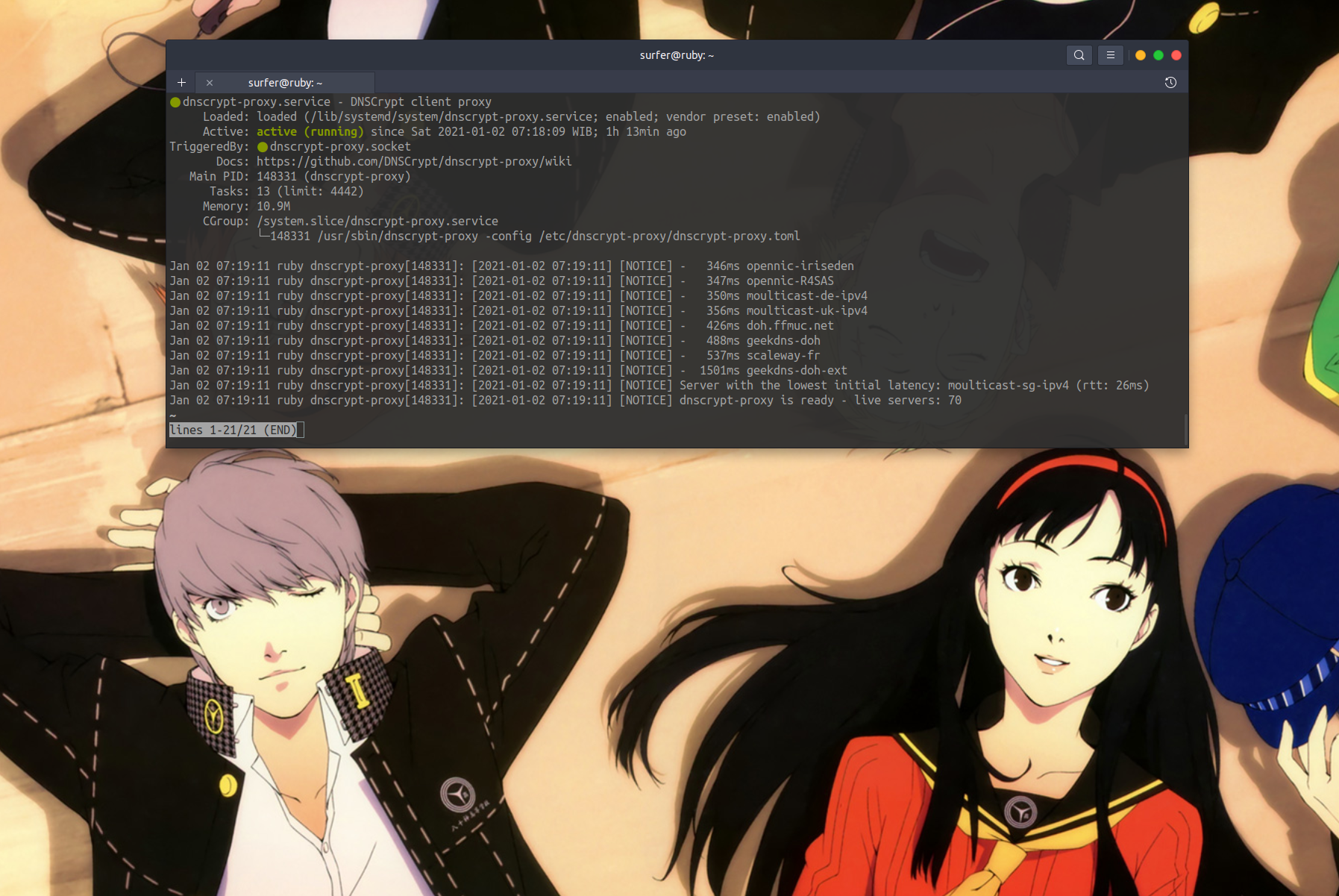
As you can see, DNSCrypt will connect you to multiple DoH and DNSCRypt servers.
Next, let’s check out on which interface DNSCrypt is active
surfer@ruby:~$ sudo netstat -plnt Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 127.0.2.1:53 0.0.0.0:* LISTEN 1/systemd tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN 81451/systemd-resol tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 80975/sshd: /usr/sb tcp6 0 0 :::22 :::* LISTEN 80975/sshd: /usr/sb
Just like our previous efforts, we will use Bind to receive and forward DNS queries from devices at your home network. Installing it is as easy as
surfer@ruby:~$ sudo apt install bind9
And configure your Bind installation, by:
sudo nano /etc/bind/named.conf.options
Point Bind to our DNSCrypt service:
acl goodclients {
192.168.10.0/24;
localhost;
};
options {
directory "/var/cache/bind";
// If there is a firewall between you and nameservers you want
// to talk to, you may need to fix the firewall to allow multiple
// ports to talk. See http://www.kb.cert.org/vuls/id/800113
// If your ISP provided one or more IP addresses for stable
// nameservers, you probably want to use them as forwarders.
// Uncomment the following block, and insert the addresses replacing
// the all-0's placeholder.
allow-query { goodclients; };
forwarders {
127.0.2.1;
};
// forwarders {
// 0.0.0.0;
// };
//========================================================================
// If BIND logs error messages about the root key being expired,
// you will need to update your keys. See https://www.isc.org/bind-keys
//========================================================================
dnssec-enable yes;
dnssec-validation yes;
auth-nxdomain no; # conform to RFC1035
listen-on-v6 { any; };
};
Ensure that the subnet block of your home network is whitelisted, and then restart the service
sudo systemctl restart bind9
Check if it’s up:
surfer@ruby:~$ sudo netstat -plnt | grep named tcp 0 0 192.168.10.150:53 0.0.0.0:* LISTEN 149130/named tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 149130/named tcp 0 0 127.0.0.1:953 0.0.0.0:* LISTEN 149130/named tcp6 0 0 fe80::2ce:39ff:fecd::53 :::* LISTEN 149130/named tcp6 0 0 ::1:53 :::* LISTEN 149130/named tcp6 0 0 ::1:953 :::* LISTEN 149130/named
You should now have a local DNS servers that forward your queries through DoH. The last thing we need to do is to change your home network DHCP server configuration so that every devices on it will use it. Here’s how it looks on my Deco M5